In an earlier post, I showed you how to configure IPSec based on a cryptomap between two routers (link here). Now I am going to show you how to add a second IPSec tunnel on the same router. Remember the obligatory rule: one crypto map per interface.
Let’s look again on topology:
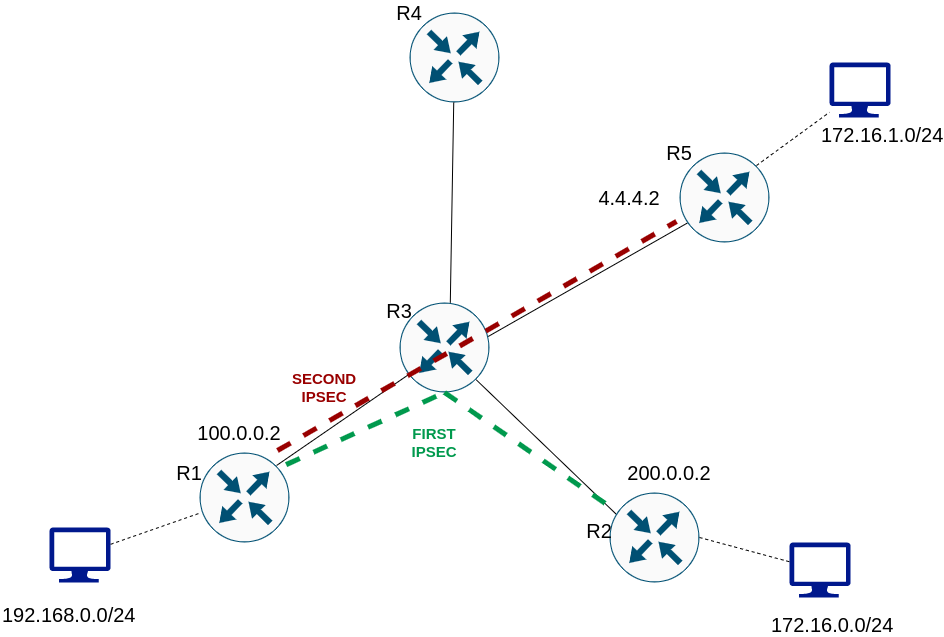
The configuration of IPSec on router R5 is similar to that on router R2:
R5#show running-config | section crypto
crypto isakmp policy 10
encr aes
hash sha256
authentication pre-share
group 24
crypto isakmp key password address 100.0.0.2
crypto ipsec transform-set TS01 esp-des esp-sha-hmac
mode tunnel
crypto map crypto_map 10 ipsec-isakmp
set peer 100.0.0.2
set transform-set TS01
match address VPN01
crypto map crypto_map
On router R1, I have configured a second IPsec tunnel. As a reminder, below is the configuration of the IPsec tunnel between R1 and R2.
R1#show running-config | section crypto
crypto isakmp policy 10
encr aes
hash sha256
authentication pre-share
group 24
crypto isakmp key p@ssw0rd address 200.0.0.2
crypto ipsec transform-set ESP_SHA512 esp-aes esp-sha512-hmac
mode tunnel
crypto map crypto_map 10 ipsec-isakmp
set peer 200.0.0.2
set transform-set ESP_SHA512
match address VPN
What do we need to do in order to add a second IPsec tunnel on router R1:
- Configure the crypto isakmp policy.
- Set up a password for the new peer.
- Configure new algorithms for the second phase of IPsec.
- Create a new crypto map (+ ACL) and assign it to an interface on the router.
Crypto isakmp policy
Now, I am going to configure a second connection with router R5. I have to add a few things to my config. We need to determine the algorithms to be used for Phase 1. In my case, I will use the same algorithms that I used to establish the connection for my first IPSec.
Let’s look below:
R1#show running-config | section crypto crypto isakmp policy 10 encr aes hash sha256 authentication pre-share group 24
Everything will be fine because the second side (router R5) has the same Phase 1 IPSec configuration. If we want to set up a tunnel with a router that has different configured algorithms, we will need to add a new ‘crypto isakmp policy’ to our configuration with the new algorithms.
When establishing a connection, the router checks the ‘crypto isakmp policy’ from top to bottom and verifies the configured algorithms. If the router finds a policy with the proper algorithms, it can establish the Phase 1 IPSec connection.
Password for peer
crypto isakmp key password address 4.4.4.2
Algorithms for second phase of IPsec and mode (tunnel or transport)
crypto ipsec transform-set TS01 esp-des esp-sha-hmac mode tunnel
R1(cfg-crypto-trans)#mode ? transport transport (payload encapsulation) mode tunnel tunnel (datagram encapsulation) mode
Configuration of crypto map + ACL
crypto map crypto_map 20 ipsec-isakmp set peer 4.4.4.2 set transform-set TS01 match address VPN01
!
ip access-list extended VPN01 permit ip 192.168.0.0 0.0.0.255 172.16.1.0 0.0.0.255
My crypto map “crypto_map” have been already assigned to interface:
R1#show running-config interface fastEthernet 0/0
Building configuration...
Current configuration : 107 bytes
!
interface FastEthernet0/0
ip address 100.0.0.2 255.255.255.252
duplex half
crypto map crypto_map
end
and look like this:
!
crypto map crypto_map 10 ipsec-isakmp
set peer 200.0.0.2
set transform-set ESP_SHA512
match address VPN
crypto map crypto_map 20 ipsec-isakmp
set peer 4.4.4.2
set transform-set TS01
match address VPN01
!
I can do little verification by typing “show crypto map”:
R1#show crypto map
Crypto Map IPv4 "crypto_map" 10 ipsec-isakmp
Peer = 200.0.0.2
Extended IP access list VPN
access-list VPN permit ip 192.168.0.0 0.0.0.255 172.16.0.0 0.0.0.255
Current peer: 200.0.0.2
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Transform sets={
ESP_SHA512: { esp-aes esp-sha512-hmac } ,
}
Crypto Map IPv4 "crypto_map" 20 ipsec-isakmp
Peer = 4.4.4.2
Extended IP access list VPN01
access-list VPN01 permit ip 192.168.0.0 0.0.0.255 172.16.1.0 0.0.0.255
Current peer: 4.4.4.2
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Transform sets={
TS01: { esp-des esp-sha-hmac } ,
}
Interfaces using crypto map crypto_map:
FastEthernet0/0
Let’s see again complete configuration of ipsec:
#show running-config | section crypto
crypto isakmp policy 10
encr aes
hash sha256
authentication pre-share
group 24
crypto isakmp key p@ssw0rd address 200.0.0.2
crypto isakmp key password address 4.4.4.2
crypto ipsec transform-set ESP_SHA512 esp-aes esp-sha512-hmac
mode tunnel
crypto ipsec transform-set TS01 esp-des esp-sha-hmac
mode tunnel
crypto map crypto_map 10 ipsec-isakmp
set peer 200.0.0.2
set transform-set ESP_SHA512
match address VPN
crypto map crypto_map 20 ipsec-isakmp
set peer 4.4.4.2
set transform-set TS01
match address VPN01
crypto map crypto_map
R1#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 4.4.4.2 100.0.0.2 QM_IDLE 1001 ACTIVE 200.0.0.2 100.0.0.2 QM_IDLE 1002 ACTIVE
END.
