-
The configuration of IPSec can be accomplished through the following six steps:
- Configuration crypto isakmp policy
- Configuration password for peer
- Configuration transform-set
- Configuration crypto map
- Configuration interface
- Configuration ACL
-
Below I will provide an example configuration for each step:
Configuration crypto isakmp policy
crypto isakmp policy 10
encr aes
hash sha256
authentication pre-share
group 24
Configuration password for peer
crypto isakmp key p@ssw0rd address 200.0.0.2
Configuration transform-set
crypto ipsec transform-set ESP_SHA512 esp-aes esp-sha512-hmac
mode tunnel
Configuration crypto map
crypto map crypto_map 10 ipsec-isakmp
set peer 200.0.0.2
set transform-set ESP_SHA512
match address VPN
Configuration interface
interface FastEthernet0/0
crypto map crypto_map
Configuration ACL
ip access-list extended VPN
10 permit ip 192.168.0.0 0.0.0.255 172.16.0.0 0.0.0.255
-
Below is the topology where I have configured the router R1.
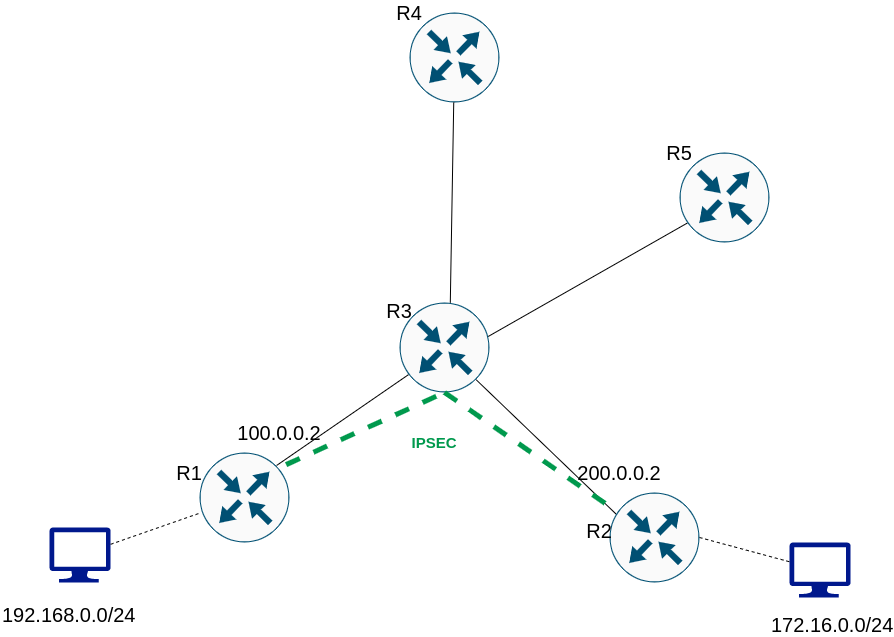
The tunnel based on crypto map has been configured between router R1 and router R2. ACLs on routers R1 and R2 capture traffic from subnets 192.168.0.0/24 and 172.16.0.0.
R1#show ip access-lists VPN
Extended IP access list VPN
10 permit ip 192.168.0.0 0.0.0.255 172.16.0.0 0.0.0.255
R2#show ip access-lists VPN
Extended IP access list VPN
10 permit ip 172.16.0.0 0.0.0.255 192.168.0.0 0.0.0.255
-
We can check the configuration by typing:
#show running-config | section crypto
crypto isakmp policy 10
encr aes
hash sha256
authentication pre-share
group 24
crypto isakmp key p@ssw0rd address 200.0.0.2
crypto ipsec transform-set ESP_SHA512 esp-aes esp-sha512-hmac
mode tunnel
crypto map crypto_map 10 ipsec-isakmp
set peer 200.0.0.2
set transform-set ESP_SHA512
match address VPN
-
Troubleshooting
- show crypto isakmp sa
- show crypto session
- show crypto ipsec sa
- show crypto map
All of the commands below were executed on a properly working IPSec.
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
200.0.0.2 100.0.0.2 QM_IDLE 1001 ACTIVE
R1#show crypto session
Crypto session current status
Interface: FastEthernet0/0
Session status: UP-ACTIVE
Peer: 200.0.0.2 port 500
IKEv1 SA: local 100.0.0.2/500 remote 200.0.0.2/500 Active
IPSEC FLOW: permit ip 192.168.0.0/255.255.255.0 172.16.0.0/255.255.255.0
Active SAs: 2, origin: crypto map
R1#show crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: crypto_map, local addr 100.0.0.2
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.0.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.0.0/255.255.255.0/0/0)
current_peer 200.0.0.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 2, #pkts encrypt: 2, #pkts digest: 2
#pkts decaps: 2, #pkts decrypt: 2, #pkts verify: 2
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.0.2, remote crypto endpt.: 200.0.0.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0x3C20819A(1008763290)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x9F65E9CE(2674256334)
transform: esp-aes esp-sha512-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80004040, crypto map: crypto_map
sa timing: remaining key lifetime (k/sec): (4297204/2981)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x3C20819A(1008763290)
transform: esp-aes esp-sha512-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80004040, crypto map: crypto_map
sa timing: remaining key lifetime (k/sec): (4297204/2981)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R1#show crypto map
Crypto Map IPv4 "crypto_map" 10 ipsec-isakmp
Peer = 200.0.0.2
Extended IP access list VPN
access-list VPN permit ip 192.168.0.0 0.0.0.255 172.16.0.0 0.0.0.255
Current peer: 200.0.0.2
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Transform sets={
ESP_SHA512: { esp-aes esp-sha512-hmac } ,
}
Interfaces using crypto map crypto_map:
FastEthernet0/0
At the end, we can check the communication between PC1 and PC2. Below is the output of the ping command and trace.
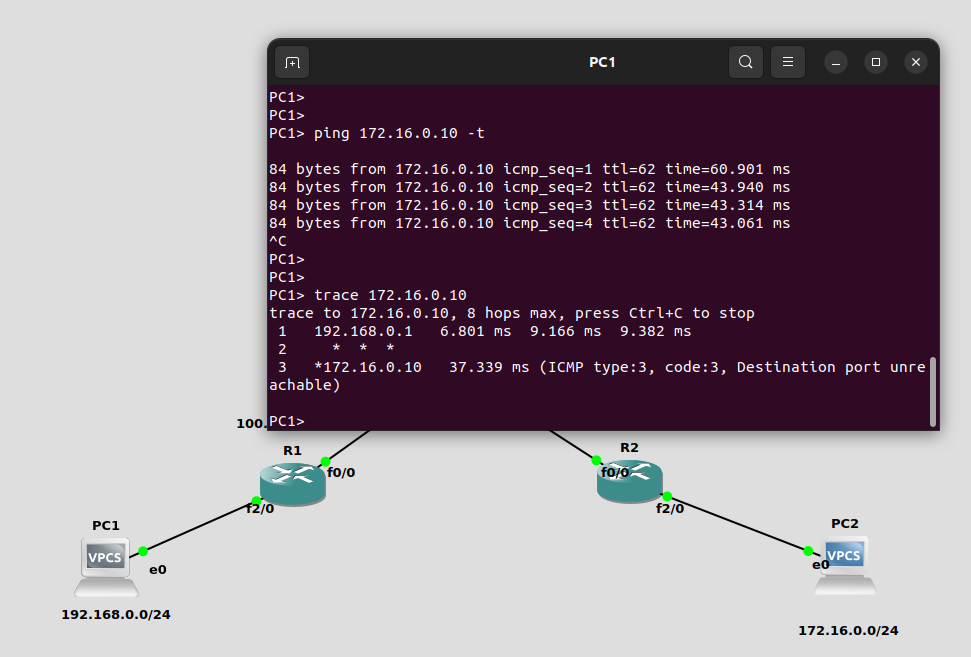
END.
